12
Mar
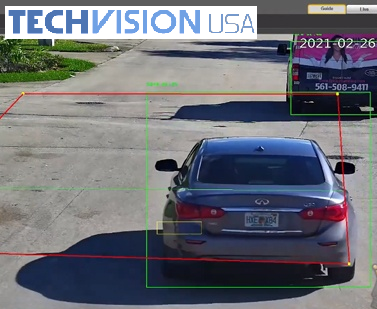
Smart Motion Detection Cameras
Security Camera King carries cameras with incredible features for security, such as Smart Motion Detection Cameras also known as SMD+!
Motion Detection is a technology that has been utilized for years to...